各种合规要求中都对用户策略有着要求,什么PCI啊,上市审计啊,都有着密码复杂程度的要求:
CentOS 7 的用户密码策略:
修改vi /etc/pam.d/system-auth
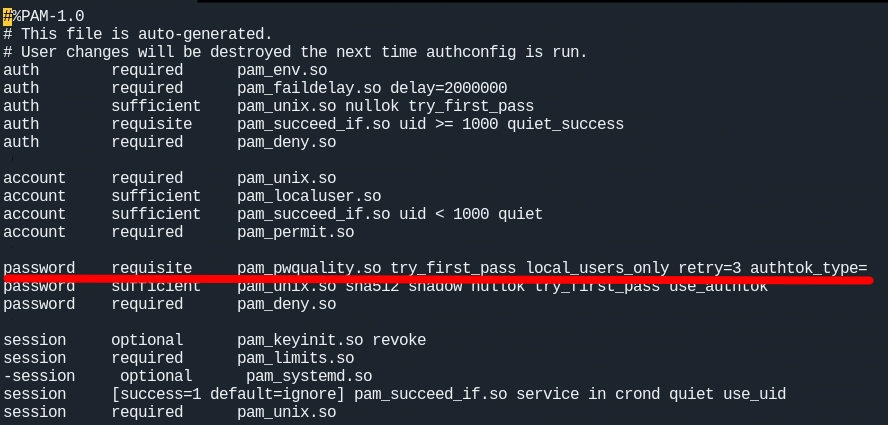
其中有一行:
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=
后面加上:
minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1 enforce_for_root
修改成为:
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type= minlen=12 lcredit=-1 ucredit=-1 dcredit=-1 ocredit=-1 enforce_for_root
意思是:
密码长度12,须包含:一个小写字符,一个大写字符,一个数字,一个特殊字符,强制root也遵守此规则
参数全部解释如下:
retry=3: This option will prompt the user 3 times before exiting and returning an error.
minlen=12: This specifies that the password cannot be less than 12 characters.
maxrepeat=3: This allows implies that only a maximum of 3 repeated characters can be included in the password.
ucredit=-1: The option requires at least one uppercase character in the password.
lcredit=-1: The option requires at least one lowercase character in the password.
dcredit=-1: This implies that the password should have at last a numeric character.
ocredit=-1: The option requires at least one special character included in the password.
difok=3: This implies that only a maximum of 3 character changes in the new password should be present in the old password.
reject_username: The option rejects a password if it consists of the username either in its normal way or in reverse.
enforce_for_root: This ensures that the password policies are adhered to even if it’s the root user configuring the passwords.